You can’t imagine, not being online. From Instagram to FaceTime, from homeschooling to working from home, virtually everything you need as a person or company in everyday life requires reliable online connectivity.
Cisco Meraki cloud-managed devices help you do this by making your network more understandable, manageable, and secure. We’ll explain how that works with the following examples:
Insight
Cisco Meraki offers great tools that provide insight into data traffic and usage.
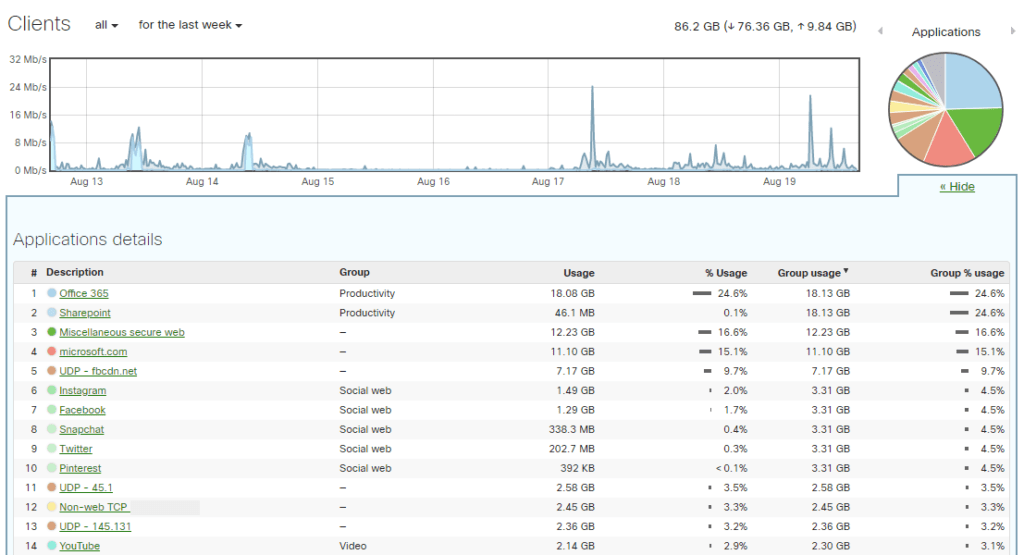
How much data traffic is garnered by guest use? Do my Office 365 applications get enough priority over other traffic? Does my Internet connection offer enough capacity for all those home workers?
The Meraki online dashboard provides answers to these questions at a glance. Traffic flows to popular services such as Office 365, SharePoint and YouTube are continuously monitored and shown in the dashboard, as well as the data consumption of individual devices in the network itself. With this information, you can then focus on optimizing the performance of these services, or that of your network as a whole.
Manageability
The Meraki dashboard’s management tools offer a range of options to optimally align network traffic and usage with your organization’s usage pattern. Here are a few examples of how you can achieve this:
- Using a second internet connectionWith the use of two separate Internet connections, you have instant redundancy for Internet connectivity. In addition, you can also use the second Internet connection to send non-critical traffic, such as the Internet traffic of guest users. It can also be used as a dedicated connection for real-time applications such as VOIP or Remote Desktop, whereby all other traffic is sent over the primary connection and can therefore not get in the way of real-time traffic.
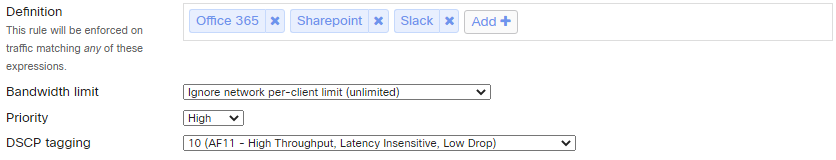
- Reducing bandwidth usage for applications and network segmentsIf you want to allow traffic to social media services but want to limit bandwidth usage, you can easily regulate this with a so-called traffic shaping policy. Specify the type of traffic to be curtailed, the maximum bandwidth usage and from then on the policy will be actively applied. This can be set for applications as well as for specific network segments such as a guest network
- Prioritize traffic for applications and network segmentsOf course, you always want to prioritize business-critical online applications over a busy internet connection, without limiting bandwidth usage. This is also easy to set up in the dashboard. In this case, you specify the type of traffic and priority.
Security
Security has already been discussed extensively in our other blogs. Rightly so, because in these times it is simply a must to have this properly set up. Network security plays a vital role in this, and in the following examples we will explain how Cisco Meraki devices can play a role in this.
- Network access for authorized devicesThe use of complex passwords and multi-factor authentication is always recommended to prevent malicious parties from accessing your login details. But did you know that it is not even necessary to have the login details of a user account to harvest sensitive information from the network? By simply connecting a computer to the network with a cable, a malicious user can retrieve passwords and other sensitive information using freely available hacking tools. Cisco Meraki switches support RADIUS authentication to prevent such intrusion attempts. Simply put, if you connect a device to the network, the device will need to authenticate itself first. If not, the device will automatically be placed in a completely isolated network segment, securely separated from the regular office network. This prevents unknown devices from misbehaving on your network. By using RADIUS, you can have devices authenticated against the built-in Meraki user database or even against Active Directory. In the latter case, the device can be authenticated with a username and password or the MAC address of the device itself.
- Group policies
Meraki group policies allow you to set up network security at user, network segment or device level. For example, the firewall rules in the policy below ensure that guest users do not have access to the office network; they allow up to 10Mb/s of bandwidth usage; they block the use of peer-to-peer and online file-sharing services.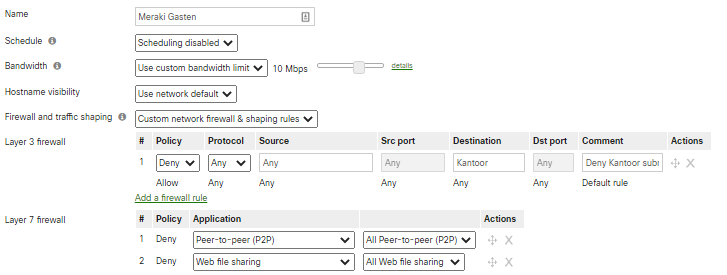
Once you have set a policy, you can assign it to wireless devices, network segments and users. In the latter case, you can even link the policy to Active Directory users and groups. For example, you can set up an entire network security department by white- or blacklisting specific websites and categories for this group of users. - Meraki Advanced Security
The Meraki Advanced Security licence adds an extra layer of security that shouldn’t be missing on any network:- Up-to-date and malware protection
- Intrusion detection and prevention
- Blocking of specific website categories
- Black- and whitelisting of websites
- Blocking of Internet traffic from and to geographic locations
The Meraki dashboard provides a clear overview of all intrusion attempts, malware detection and quarantine, and attempts to access blocked websites and categories.
Building a secure network
Everything clearly arranged in one dashboard and the possibility to arrange everything in a safe and orderly way. Recently we have been able to set up Cisco Meraki networks for various customers, and of course, we also like to think along with you. There are endless possibilities, but we are happy to take on the challenge of finding the right solution for your organization. Would you like to know more? Please contact us, or leave us a callback request.